Configure IdentityNow Service Account in BeyondInsight
Creating an IdentityNow service account in BeyondInsight requires the following:
- Create a user group
- Enable features and Smart Groups for the user group
- Create a user account and add it to the user group
- Log in to BeyondInsight as the new service account user to generate OAuth credentials.
The below sections detail the steps to take to accomplish the above.
Create a New Group for the Service Account
To create a local group in BeyondInsight, follow the below steps:
- Navigate to Configuration > Role Based Access > User Management.
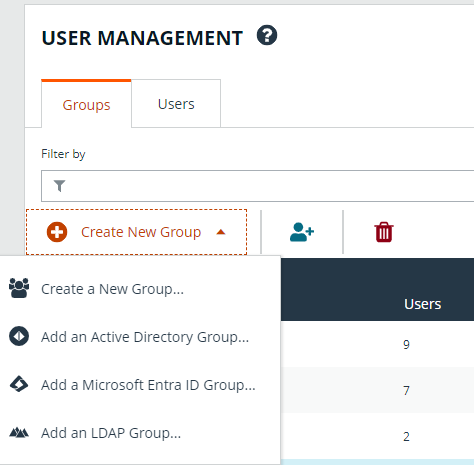
- From the Groups tab, click + Create New Group.
- Select Create a New Group.
- Enter a Group Name and Description for the group.
- Click Create Group.
- Follow the steps in the below sections to enable features and Smart Group for your newly created group.
In addition to creating groups locally, you can import Active Directory, Entra ID, and LDAP groups into BeyondInsight.
Enable Features for the Group
To enable features for a group in BeyondInsight, assign permissions to the features as follows:
- Go to Configuration > Role Based Access > User Management.
- From the Groups tab, find the group and click on the corresponding ellipsis to right of the group.
- Select View Group Details from the list.
- Click Features located under Group Details.
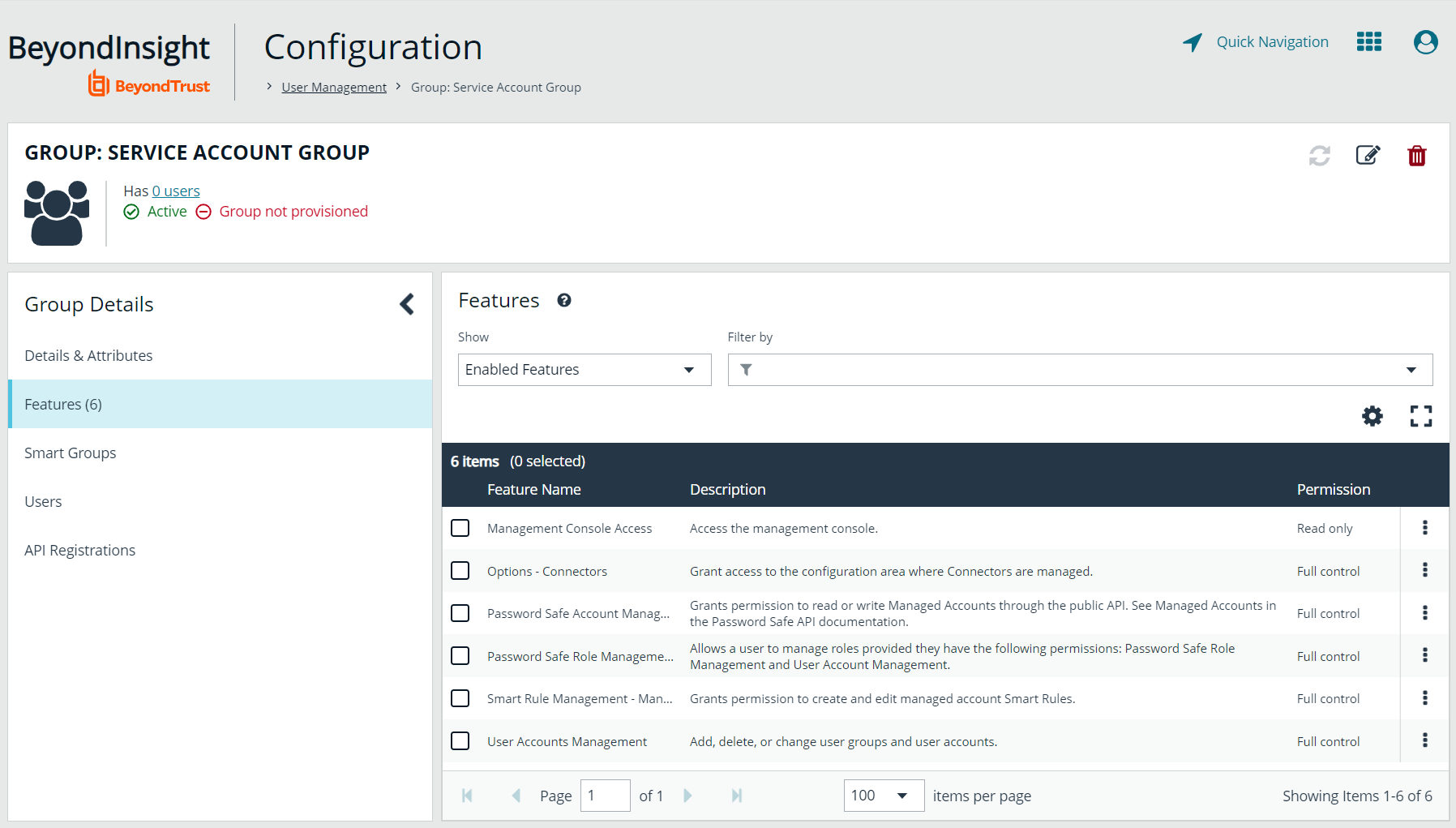
- Select All Features from the Show dropdown above the grid to display a list of features in the grid.
- Select the Management Console Access feature and click Assign Permissions > Assign Permissions Read Only above the grid. This permission is required so the service account can log in to BeyondInsight and obtain the service accounts’ unique OAuth credentials.
- Select the following features and click Assign Permissions > Assign Permissions Full Control above the grid.
- Options - Connectors: This feature is required to allow the creation of OAuth credentials by the member account. In production, this permission could be removed after connection is established, but is needed again to cycle client_secret and refresh_token.
- Password Safe Account Management: This feature is required to read or write managed accounts through the public API.
- Password Safe Role Management: This feature is required to allow visibility into account Smart Groups, which are assigned via user groups in BeyondInsight.
- Smart Rule Management - Managed Account: This feature is required to manage Smart Rules for managed accounts.
- User Accounts Management: This feature is required for the service account to manage user groups and user accounts.
Enable Smart Groups for the Group
To enable Smart Groups for a group in BeyondInsight, assign permissions to the Smart Groups as follows:
- Go to Configuration > Role Based Access > User Management.
- From the Groups tab, find the group and click on the corresponding ellipsis to right of the group.
- Select View Group Details from the list.
- Click Smart Groups located under Group Details.
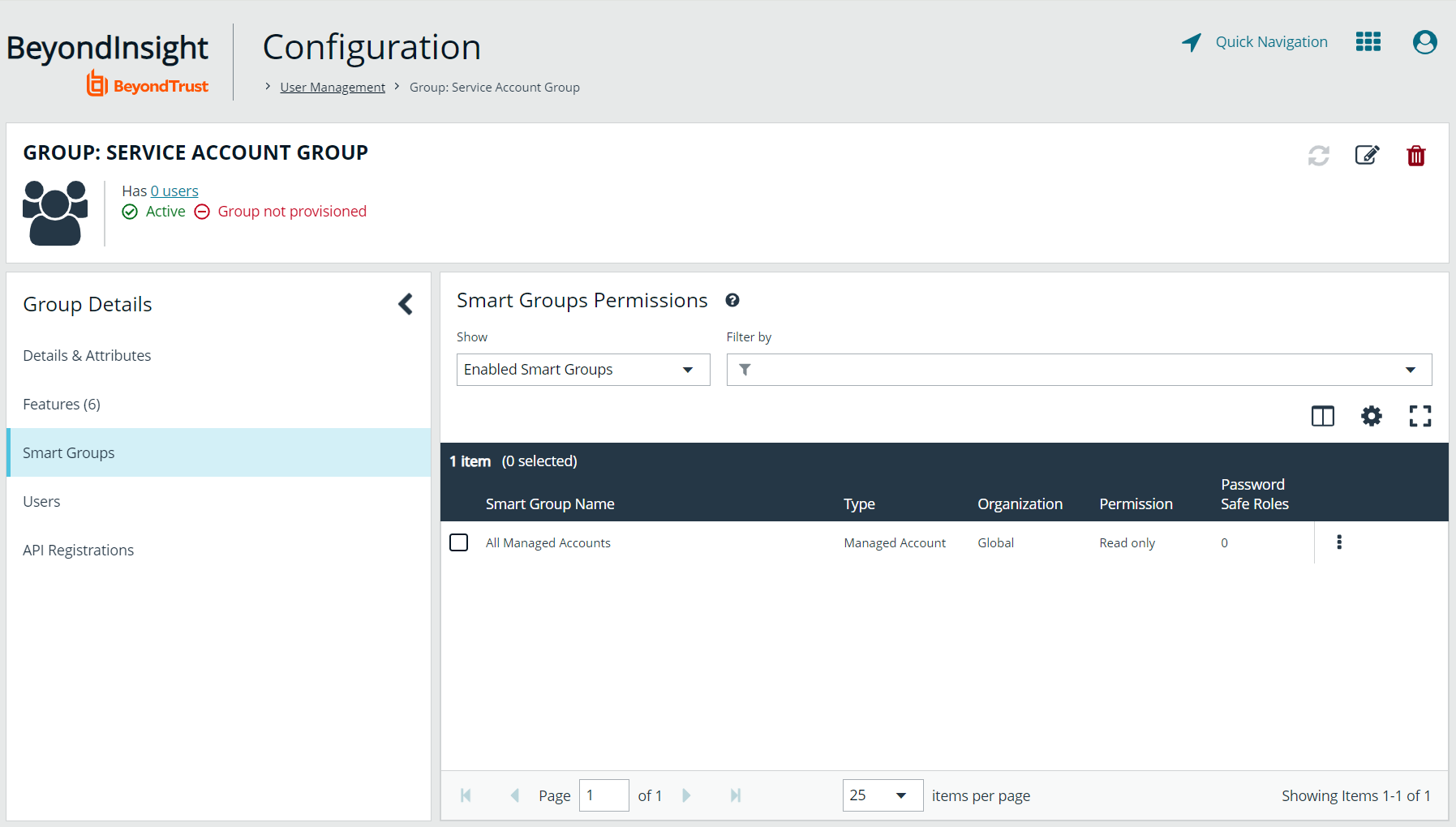
- Select All Smart Groups from the Show dropdown above the grid to display a list of Smart Groups in the grid.
- Select the All Managed Accounts Smart Group and click Assign Permissions > Assign Permissions Read Only above the grid.
Managed Account Smart Groups with a category of Managed Accounts are visible via the SCIM API. Managed Account Smart Groups with a category of Platforms are not visible. However, you can recreate the same Smart Group with a category of Managed Accounts.
Create a New User and Assign to Group
Once the group is created and assigned the appropriate features and Smart Groups permissions, you can create a new account in BeyondInsight for the service account and add it to the group.
Permissions are assigned only to the group, not to the account.
- Go to Configuration > Role Based Access > User Management.
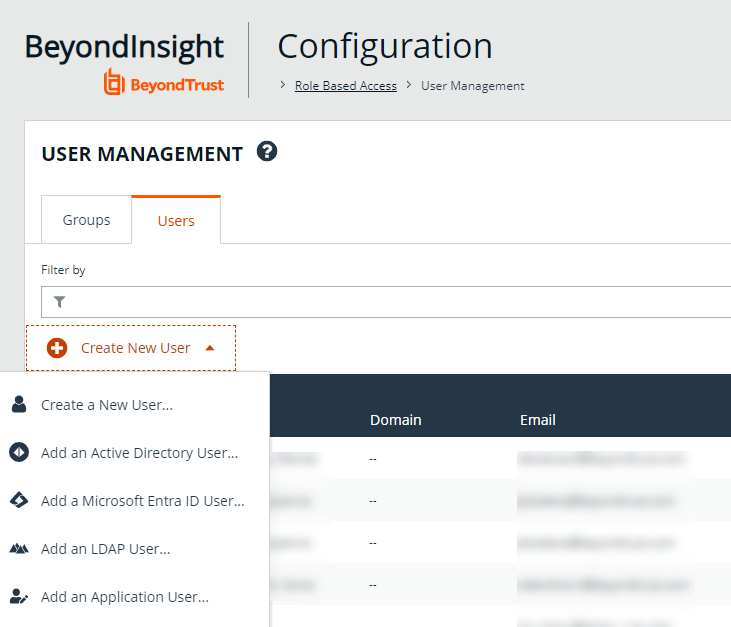
- From the Users tab, click Create New User.
- Select Create a New User.
- Provide Identification, Credentials, Contact Information, User Status, and Authentication Options as needed.
- Click Create User.
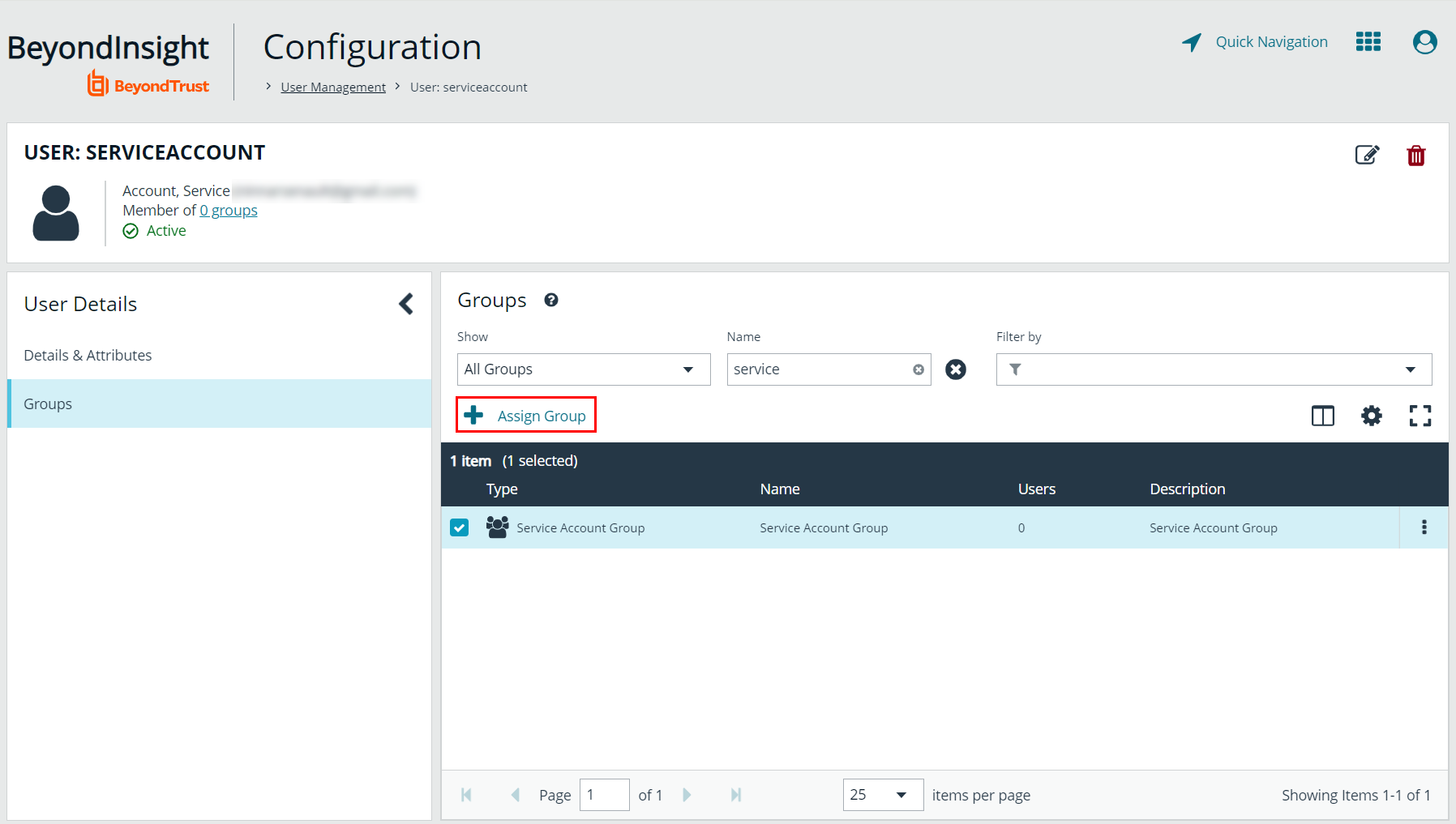
- You are taken to the details page for the user account where Groups is automatically selected. Select All Groups from the Show dropdown above the Groups grid to list all available user groups.
- Locate the group you created above for the service account, select it, and then click Assign Group above the grid.
In addition to creating user accounts locally, you can import AD, Entra ID, and LDAP accounts and add them to either local or imported groups.
Generate OAuth Credentials
Once the user account is created and assigned to a group, you must log in as the new user to generate OAuth credentials.
- Go to Configuration > General > Connectors.
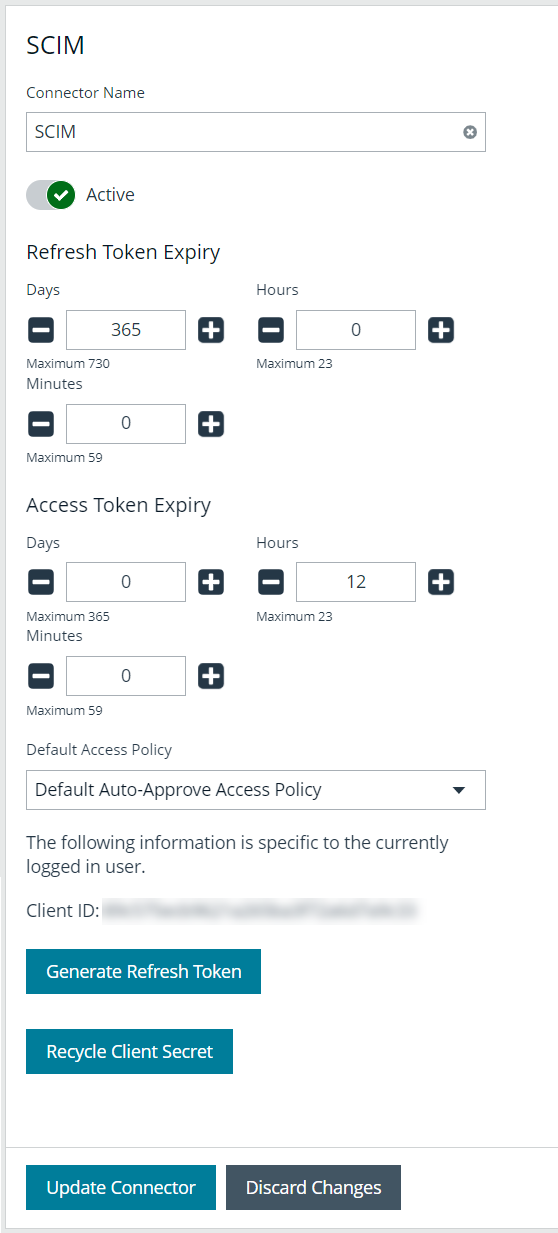
- Under Connectors, select the SCIM connector. Once selected, the SCIM connector information displays.
Do not select the SailPoint connector. This was available in previous versions of BeyondInsight, but it is an older integration and is not based on SCIM.
- Each logged-in account in BeyondInsight has a unique client ID. The Client ID is located within the SCIM connector information. Highlight the ID, right-click, and save locally as client_id to a text file.
- Click Recycle Client Secret.
- Click Recycle on the Recycle Secret Access Key pop-up. This generates a unique access key.
- Highlight the Client Secret access key, right-click, and save as client_secret to a text file.
- Click Generate Refresh Token if you want to use this method of authentication. Use the account login password when prompted.
The refresh token is used in the production environment. Client credentials (client ID and client secret) are used in a lab or test environment. Every Password Safe user with full control permissions to the Options – Connectors feature can obtain a Client ID and Client Secret via the connector.
Only one SCIM connector can be created by Password Safe per instance.