Integrate Identity Security Insights with Splunk
Identity Security Insights integrations allow you to connect third-party security information and event management (SIEM) tools to your BeyondTrust Insights console. Once an integration is configured, Insights automatically sends information regarding new detections and recommendations to the provided endpoint.
Integrating Splunk allows you to create an HTTP Event Collector which supports forwarding data and application events from Insights to a Splunk deployment over the HTTP and Secure HTTP (HTTPS) protocols.
Splunk investigates, monitors, and analyzes data from any source. Use Splunk to search, index, and correlate big data to set up relevant alerts, reports, and visualizations.
Create a new Splunk HTTP Event Collector
- From your Splunk dashboard, navigate to Settings > Add Data, and click monitor.
- Click HTTP Event Collector, and provide the following information:
- Name: a name for the new token.
- Changes to Source name override, Description, and Indexer acknowledgment are optional.
- Click Next, and confirm where you would like the new events stored. This Index is used in your integration configuration.
- Click Review, and ensure your new settings are correct.
- Click Submit.
- Copy the token value provided by Splunk Web. This is used in your integration configuration.
Add a Splunk integration in Insights
- In the header of your Insights instance, click Menu > Integrations.
- Click Splunk.
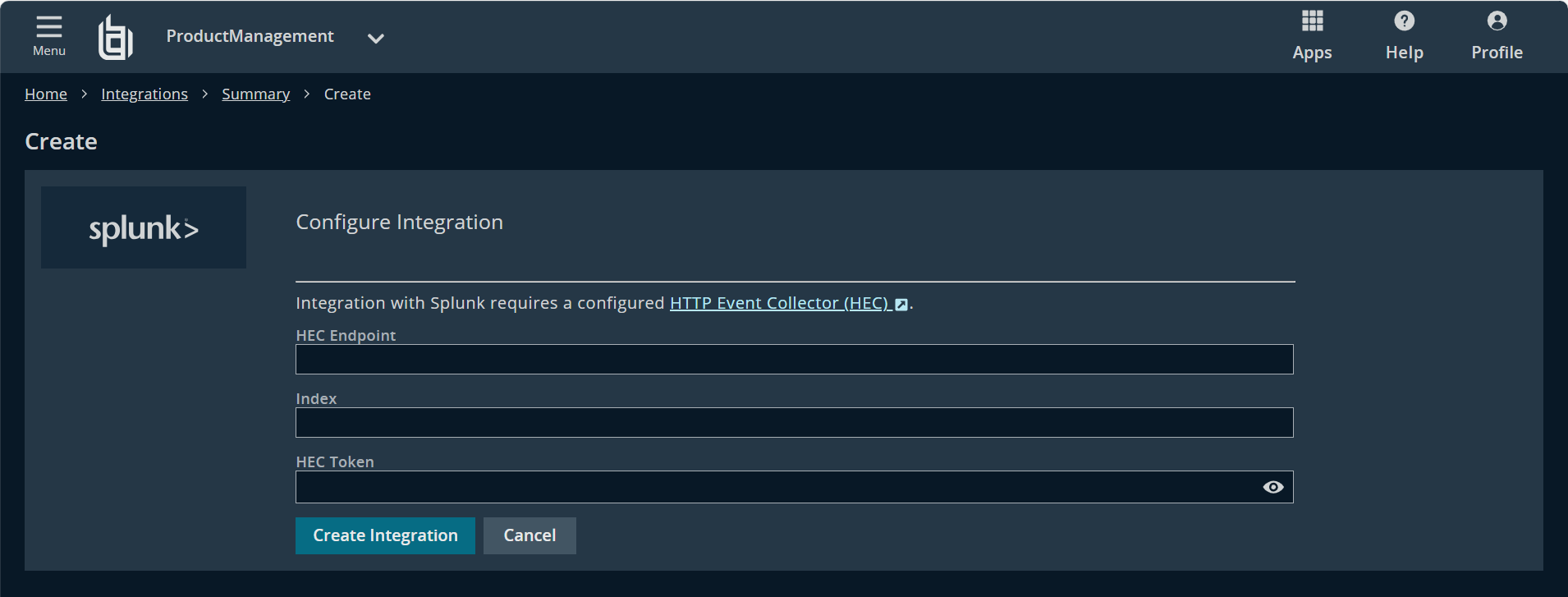
The Configure Integration page displays. - Enter the details for your Splunk configuration:
- HEC Endpoint: The hostname of your HTTP Event Collector endpoint.
- Index: The index of your HTTP Event Collector.
- HEC Token: The token created with your new HTTP Event Collector.
- Click Create Integration.
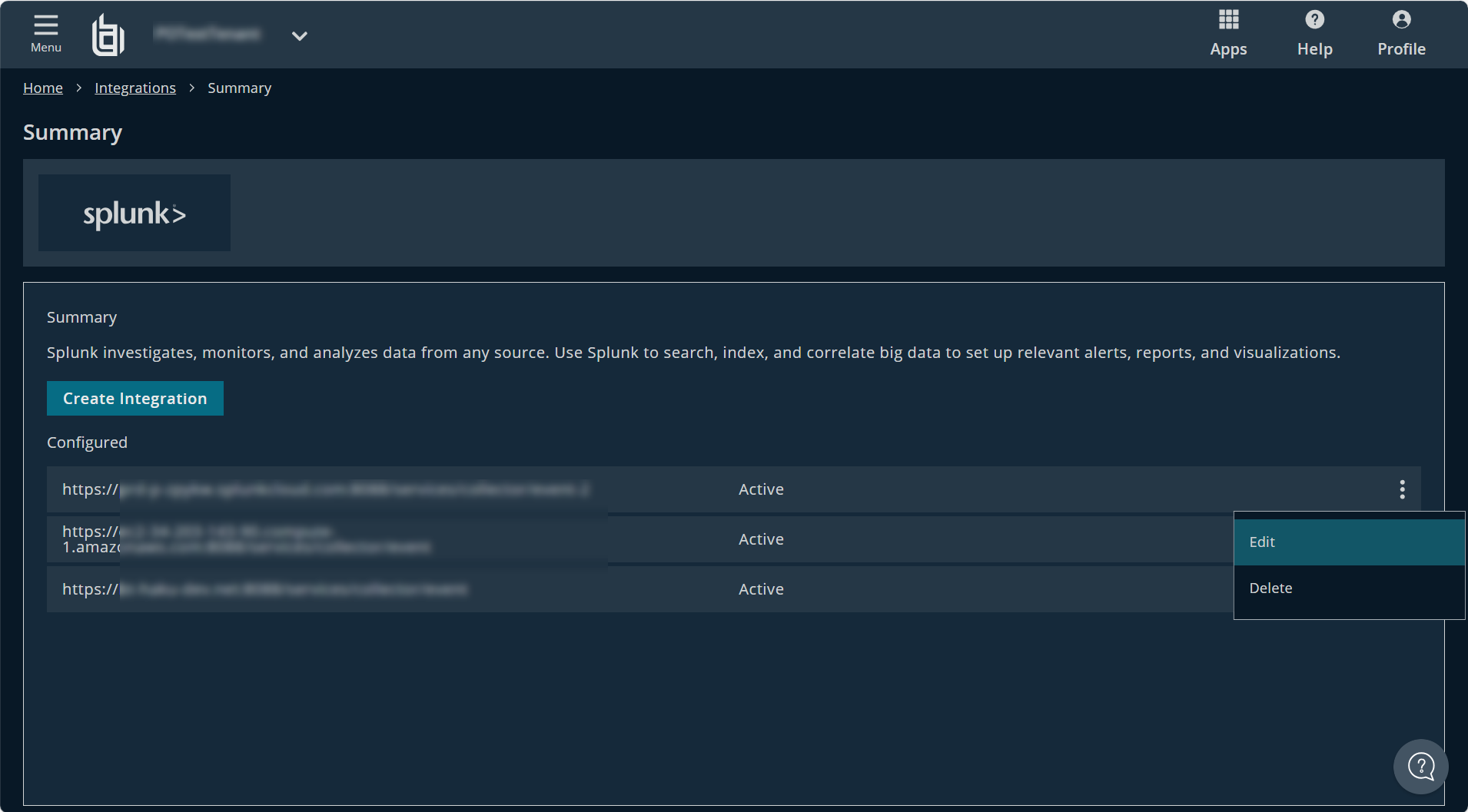
You are redirected to your Splunk integration dashboard, with your new integration added under Configured.
Edit a Splunk integration
To edit an individual Splunk integration:
- Click the vertical ellipsis for a configured integration.
- Select Edit.
The Configure Integration page displays. - Edit the Hostname, Index, and HEC Token as necessary to assist in troubleshoot failing integrations.
- Click Save Integration.
Edits to an integration may take up to two minutes to take effect.
You can remove individual Splunk integrations by deleting them. Deleting an integration cannot be undone and all of its configuration settings and data are deleted.
To delete an individual Splunk integration:
- Click the vertical ellipsis for a configured integration.
- Select Delete.
- Type delete in the box to confirm you want to delete the integration.
- Click Delete Integration.
Splunk schema mapping
| Field | Internal Mapping |
|---|---|
| message | "<incidentDescription>" |
| tags | ["Detection | Recommendation"] |
| labels | { "current_status": "<Open | Expected | FalsePositive | Resolved | InProgress>" } |
| event.id | "<incidentId>" |
| event.url | "https://app.beyondtrust.io/t/<tenantId>/detections/details/<incidentId>" |
| event.reason | "<incidentDefinitionDetail>" |
| event.severity | <incidentSeverity> |
| event.code | "<incidentDefinitionId>" |
| rule.id | "<incidentDefinitionId>" |
| rule.description | "<incidentDescription>" |
| rule.version | "<incidentDefinitionVersion>" |
| ecs.version | "8.7.0" |
| impacted_entites[i].entity_id | "<incidentImpactedEntityId>" |
| impacted_entities[i].entity_type | "<incidentImpactedEntityType>" |
| impacted_entities[i].tenant_id | "<incidentImpactedEntityTenantId>" |
| impacted_entities[i].name | "<incidentImpactedEntityName>" |
| impacted_entities[i].description | "<incidentImpactedEntityDescription>" |